EMM vs. MDM: How Will Your Enterprise Manage Mobility?
If you want to know the difference between mobile device management and enterprise mobility management, and which one to choose, this EMM vs. MDM guide is just what you need.
Is your company using the right management software for your employees’ mobile devices and applications? Perhaps you are using a legacy device-management system and wondering if it’s time to make a change.
Maybe you currently have no such solution, but need to centralize control of employees’ mobile technology to protect your enterprise, and are trying to identify the right type of platform to implement.
Decisions like these can be hard to make if you’re not a mobile technology expert. However, you may not have the luxury of abdication, so it will help to know at least a little about mobile device management (MDM) and enterprise mobility management (EMM).
You are sure to come across these two types of mobility management once you start exploring the topic. And if you want to get to grips with the similarities and differences between them, our EMM vs. MDM comparison should help you to do so.
In the Beginning, There Was MDM
Before progressing too far into the EMM vs. MDM debate, we’ll touch on the background behind the two systems, because it has been something of an evolutionary tale.
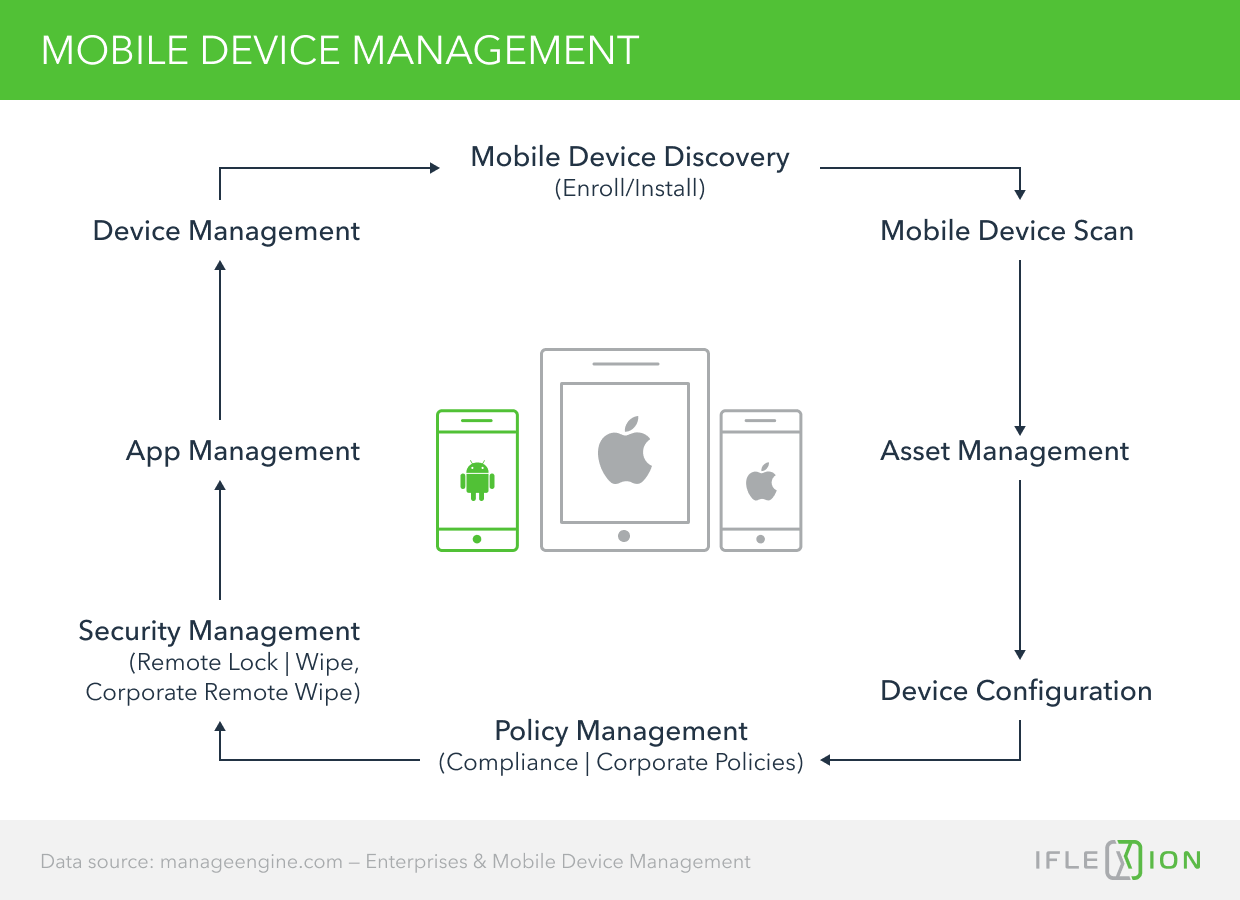
Mobile device management has been around almost as long as mobile devices have, and MDM software use grew in parallel with the adoption of smartphones and tablets as standard end-points for corporate IT and communications networks. That growth has been phenomenal and today, close to 80% of enterprises believe the use of a mobile phone is essential for their employees to work effectively, according to enterprise mobility research conducted by Samsung in 2018.
No company wants to lose control of its sensitive business data, but with employees choosing en masse to use personal devices in their jobs, it would have been seemingly inevitable without some concrete protection; hence the emergence of mobile device management solutions.
An MDM system is a central platform to which a company can link its employees’ mobile devices, including smartphones, wearables, tablets, and laptops. By insisting that all devices used for company business be enrolled on the MDM platform, a company’s IT department can control some aspects of their use.
The Strength of MDM is Also its Weakness

Perhaps most notably, enrollment on an MDM enables administrators to wipe a device of data if it was lost or stolen. Sadly, while this capability was the greatest strength of mobile device management, it also transpired to be a terminal limitation.
Because it works only at the device level, MDM has proven largely unpopular with end users, who often consider it too invasive and threatening to their privacy. One reason for this is that when a phone or tablet appears compromised, all data on that device is deleted. MDM is unable to discriminate between sensitive data belonging to the company and personal data harmless to the organization.
This weakness led to a search for more effective solutions to supersede, or integrate with, mobile device management, spurring the emergence of mobile application management and later, enterprise mobility management.
 Tweet
Tweet
EMM vs. MDM: The Similarities
So having established that EMM evolved to some extent from mobile device management, we can move on to look at the similarities and differences between them. As you might imagine from the background story, EMM has more capabilities than MDM. You could even class it as an evolved MDM. After all, an EMM will always have mobile device management functionality onboard.
Regarding general similarities though, potential buyers of either system are likely to have the same objectives—to maintain control over company-issued, or user-owned mobile devices. Mobility management platforms achieve this control by way of device and user profiles, matched to the roles of employees and applied to the enrolled phones or other mobile hardware.
After enrolling devices on the platform, MDM and EMM administrators can solve problems, push out applications, files, and notifications, upgrade software, lock devices, and delete data, all from a central hub.
While old solutions may have been quite limited in the operating systems they supported, the latest MDM products, and most EMM platforms can manage devices running any popular operating system and support thousands of device brands and models.
Core Functions Common to EMM and MDM
Aside from the broader similarities, you should expect the following specific functions to be standard in any competent device-management platform, whether it is an MDM or EMM.
Management of Device Inventory: This group of features will typically comprise device enrollment and decommissioning, as well as asset tracking. Specific inventory management functionality might include the following:
- Central visibility of asset details and change histories
- Remote device wiping, backup, and restoration
- Self-enrollment for users
Management of Device Use-Policies: EMM and MDM platforms should both enable policy management functionality, including enforcement actions and compliance checks.
Device Security Management: One of the most critical MDM/EMM functions, device security functions must protect both the integrity of users’ devices and the data they transmit, receive, and store. Features can include:
- PIN and password management
- Data encryption
- Wi-Fi, VPN, and email security
- The ability to create and maintain device blacklists
- Jailbreak detection
Activity Monitoring and Reporting: MDM and EMM platforms provide historical and real-time visibility into a company’s device inventory. They allow an IT team to know where each device is and what activities it is performing. Configurable dashboards and reporting features provide the ability to view device-activity in summary or detail and share reports with stakeholders via a range of delivery formats.
 Tweet
Tweet
EMM vs. MDM: The Differences
A discussion of the differences between MDM and EMM must necessarily tend toward an appraisal of enterprise mobility management because in most cases an EMM platform is equipped with integrated MDM, the features of which have been covered in the previous section of this article.
The differences between the two solutions are really in the additional functions and features you will find available in EMM, all of which are designed to overcome the constraints of device-level control and provide a more flexible strategy for managing employees’ mobile technology.
The need for such a transition arose mainly from the bring-your-own-device (BYOD) movement that has seen enterprises shift from issuing phones or tablets to allowing employees to use personal devices for company business. Despite the potential security risks of BYOD, the trend was irresistible for corporate employers, and in any case, if results of a study by Cisco are to be believed, BYOD delivers savings of up to $350 per employee, per year; compared with the cost of issuing company-owned mobile hardware.

EMM: A “Suite-er” Solution for BYOD
While MDM was more than satisfactory—and still is—for companies insisting that employees keep separate personal and company devices, the rise of BYOD required employers to find less invasive methods of controlling business data.
EMM emerged from that need to become the modern standard in corporate mobility management. Instead of solely controlling devices, EMM lets IT departments manage just about any combination of hardware, apps, internal web resources, and data.

Where MDM is a tool, it is more accurate to describe enterprise mobility management as a software suite, as it typically comprises an integrated collection of components for device, application, content, and authentication management. So let’s now look at the various functions and features that you will find in an EMM suite, but which are absent from mobile device management.
 Tweet
Tweet
Mobile Application Management (MAM)
Along with an MDM component, an enterprise mobility management suite will have onboard application management (MAM), which allows companies to control the use of specific apps on enrolled devices, and to ensure they are isolated from personal applications and content.
MDM facilitates this isolation by enclosing enterprise apps in a container, which spares employees’ mobile hardware from the possibility of indiscriminate data deletion while protecting business apps and data from the risk of external compromise.
Other core capabilities of MAM include:
- App installation and updates
- App usage analytics
- Push notifications
- User authentication
- App performance monitoring
- App blacklisting and whitelisting
As the above list of features may suggest, mobile application management is more about facilitation and data protection, as opposed to the more control-oriented MDM technology. However, the list of EMM capabilities (and acronyms) doesn’t end with MDM and MAM, because a good EMM suite will also include mobile content management (MCM) and perhaps even mobile identity management (MIM).
 Tweet
Tweet
Mobile Content Management (MCM)
EMM places the control of mobile devices and the applications they run in the hands of a corporate IT team, but in this connected age when data is everything, that is still not enough protection in the eyes of many senior corporate stakeholders. That’s why mobile content management is also a part of the EMM concept.
While MAM isolates mobile enterprise apps in containers, mobile content management applies a similar principle to content, such as email attachments and corporate documents. Among the BYOD problems it solves is how to allow employees to use their preferred email apps for business communication without losing control of sensitive content in attachments.
By using targeted containerization to isolate email attachments, MCM automates the control of company-related email, preventing users from accidentally or intentionally releasing proprietary content into uncontrolled environments.
Key Features of MCM Software
The following email and document protection features are typically available in EMM solutions:
- Secure on-device document storage
- Application-level data encryption
- Selective wiping of documents on a user’s device
- Device quarantining
- Blocking of the ability to cut, copy, and paste content from secure enterprise documents
- Selectively controlled access to documents for third-party apps
- Automated document back-up to the cloud
These controls are not constrained to the protection of emails, which nowadays would be a limitation indeed, given the range of tasks (see the chart below) that companies want their employees to perform on mobile devices.

For example, EMM software also secures documents contained in repositories like SharePoint, enabling employees to communicate, collaborate, access information, and share knowledge freely within the confines of the business domain, while retaining freedom over the personal use of their devices, safe in the knowledge that they will not be unwitting sources of corporate data leaks.
 Tweet
Tweet
Mobile Identity Management (MIM)
Many EMM solutions come equipped with mobile identity management to complete the suite of protective services and controls. The core function of MIM is to provide device users with a single sign-on for all enterprise applications to which they are granted access.
The technology generates strong passwords for the applications but does not provide the user with the password details. The MIM software changes passwords regularly for added security, and MIM may use two-factor authentication, which requires a user to enter a one-time password, or OTP (sent to his or her phone) to log into protected applications.

Access to applications is based on predefined user-roles, and some solutions include geo-fencing capabilities to control app-access by location and one-touch push authentication, which is a more user-friendly two-phase authentication method than OTP, as it requires no password or PIN to be input, instead needing only the push of a button to acknowledge receipt of the push notification.
 Tweet
Tweet
Should You Ever Need to Decide on EMM vs. MDM?
It should be clear from the comparisons drawn in this article that the difference between mobile device management and enterprise mobility management is significant. Any EMM solution worth having will include full device management functionality, whereas an MDM product will almost certainly have no capabilities beyond those needed to control a device as an inclusive whole.
You may be wondering at this point if there would ever be a reason to opt for MDM if you need to manage a fleet of company-assigned or personal devices used across your organization. The answer to that question will probably depend on what kind of mobile devices you need to control and their intended purpose.
Is There Still a Place for Standalone MDM?
Mobile device management can be very suitable for a fleet of mobile terminals such as those used in home delivery or warehouse management. These devices are only likely to connect to your internal network, and there will be no requirement to isolate corporate from personal apps, content, or data.
You could also stretch an MDM solution to managing phones and tablets if you only allow the use of devices owned and issued by your company, although even then, you would enjoy much more flexibility of control with an EMM platform. If your company maintains a BYOD policy or uses a mix of BYOD and corporate-issued devices, a product that allows only device management may not be especially useful.
On its own, mobile-device management might limit your ability to support remote working and could negatively affect user satisfaction. Furthermore, it may not protect your enterprise effectively if device-users are connecting to random networks, cloud applications, and remote servers to interact with your corporate data.
 Tweet
Tweet
MDM Should be the Minimum Standard
Whether you believe that your organization can settle for MDM or would benefit more from the comprehensive capabilities of EMM, any enterprise mobility solution will be better than none. That’s unless your business has no use at all for mobile devices—and if that were the case, you probably would not have been reading this article.
So our recommendation—especially if your enterprise is among the 20% that Enterprise Mobility Exchange survey statistics revealed as having no mobile device policy or management technology in place—is to use our comparison as a guide to draw your own EMM vs MDM conclusions—and prepare to invest in the solution that best meets your company’s needs and budget.
 Tweet
Tweet
Iflexion's experts will help you pick the best match
-
![]()
How to Choose the Right Enterprise Learning Management System
A good LMS will help your employees learn quickly and efficiently. In this article, we explore what makes an LMS good and how to create one.
FULL ARTICLEUpdated: September 08, 2022Published: July 25, 2018By Maria Dorogokupets
WANT TO START A PROJECT?
It’s simple!
